The financial sector is under constant pressure to strike the right balance between strong security, regulatory compliance, and frictionless user experience. Traditional methods like passwords, SMS OTPs, and even basic 2FA are increasingly seen as weak, costly, and prone to fraud.
That’s why banks are now turning to FIDO-based authentication, including passkeys.
But as with any security technology, success depends on how you implement it. This post breaks down how banks can apply FIDO securely—and responsibly—for high-stakes financial services.
FIDO: A Quick Recap
FIDO (Fast Identity Online) is an open authentication standard based on public key cryptography. It eliminates the need for shared secrets (like passwords) by using:
- A private key stored on the user’s device (in secure hardware)
- A public key stored on the server
- Biometric or PIN verification, all local to the device
The newer passkeys standard builds on FIDO2 to support secure, synced credentials across devices (e.g., via iCloud Keychain or Google Password Manager). Please read also why Fido is the future of secure authentication.
Why FIDO Is a Good Fit for Banks
- Phishing-resistant by design: Credentials can’t be reused or stolen.
- User-friendly: No need to remember or type passwords.
- Privacy-preserving: Biometrics and PINs stay on the device.
- Reduces fraud and support costs: No reset flows, no weak second factors.
But: banks can’t treat FIDO as a plug-and-play replacement. Let’s explore how to apply it securely.
1. Use Hardware-Backed Authenticators
Why it matters: Secure banking requires high assurance that the credentials and biometric verification occur in a tamper-resistant environment.
✅ Best Practices
- Require platform authenticators (e.g., Secure Enclave on iOS, TPM on Windows)
- Reject or flag non-hardware-based authenticators
- Enforce device attestation
🔍 Device attestation is a process where the authenticator proves to the server that it is a legitimate, certified piece of hardware. This helps prevent untrusted or malicious devices from being used to authenticate.
✅ Example: Only allow FIDO credentials from verified authenticators like Android Keystore, Apple Secure Enclave, or external FIDO2 security keys.
2. Enforce Local User Verification (Biometric or PIN)
FIDO enables login only after local verification (e.g., fingerprint, Face ID, device PIN).
✅ Best Practices
- Enforce user verification (UV) = required in your FIDO/WebAuthn policy
- Never accept credentials where
userVerified = false - Use policy enforcement to block weak or bypassed verification methods
🔍 Policy enforcement means configuring the authentication backend (typically your WebAuthn or FIDO2 server) to only accept credentials and authenticator responses that meet your institution’s security requirements. This includes requiring hardware-backed authenticators, enforcing local biometric or PIN checks, rejecting unverifiable devices, and disallowing low-assurance or emulated environments.
For example: You might configure your policy to allow only platform authenticators with user verification set to “required”, device attestation that matches known trusted vendors, and block any authentication attempts from devices without secure hardware.
3. Handle Device Loss Securely
Passkeys can be synced across devices (e.g., iCloud, Google Password Manager), which increases usability—but you must manage the risk of lost or stolen devices.
✅ Best Practices
- Let users view and revoke registered devices
- Use push verification or Document Authentication (DocAuth) for secure recovery
🔍 DocAuth refers to verifying a person’s identity by scanning a government-issued ID and performing face matching or liveness checks. It’s useful as a fallback when the original device is lost.
- Consider transaction confirmation for high-value operations
4. Device Management, Migration, and Enrollment
Device Management
Users should have access to a device management dashboard within their banking app or online portal where they can:
- See all registered devices with details like device type, model, last used date, and registration date
- Revoke any device remotely if lost or compromised
- Receive notifications about suspicious activity on any device
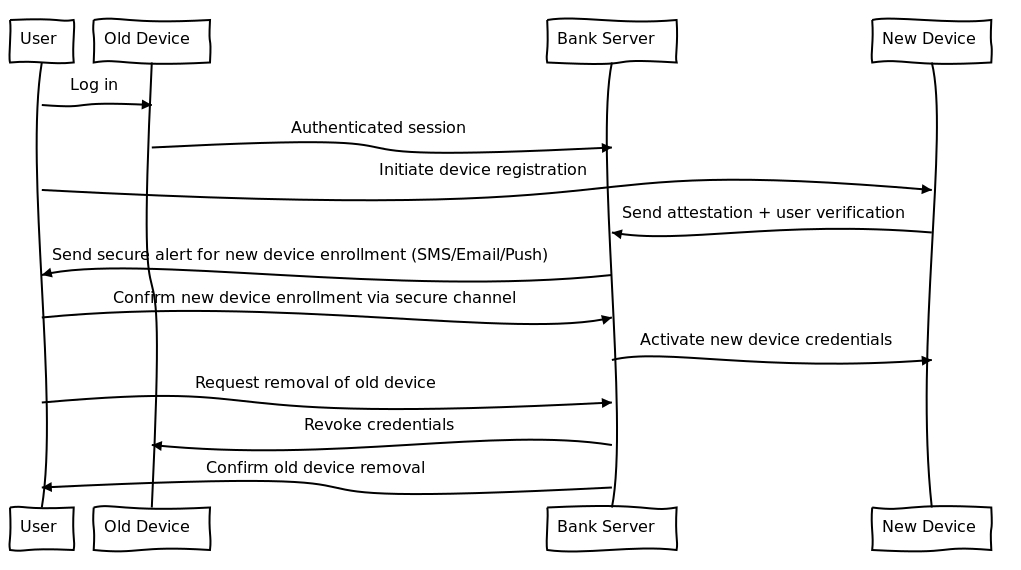
Device Migration (Old to New Device)
When users upgrade or replace their device:
- Encourage them to register the new device while still logged in on the old device
- Enforce device attestation and user verification on the new device before registration is accepted
- Notify the user via secure alerts about the new device registration
- Once the new device is confirmed, allow the user to remove the old device from their account
- If the old device is unavailable (lost or wiped), use DocAuth or other recovery methods to verify identity before enabling new device enrollment
Device Enrollment After Device Loss
If a user loses their device:
- They initiate enrollment from a trusted recovery channel (web portal or customer service)
- The bank requires identity verification using DocAuth or similar KYC methods
- After verification, the user can register a new device
- All new device enrollments trigger secure alerts to notify the user of the change
- Optionally require step-up authentication (e.g., a phone call, one-time passcode) to prevent fraud
Send Alerts for New Device Enrollments (Securely)
When a user adds a new device to their bank account for FIDO/passkey authentication, it’s critical to notify them immediately. This helps detect and block unauthorized access early.
How to Send Secure Alerts
- Out-of-Band Communication Channels Use a communication channel separate from the device or browser used for enrollment to avoid attackers intercepting or spoofing alerts.
- SMS to the registered phone number
- Email to the verified email address
- Push notification to a previously enrolled trusted device
- Include Actionable Details Alerts should include:
- The device type and model (if available)
- The approximate location or IP address of the enrollment
- The time and date of registration
- Require User Acknowledgment Provide a secure way for users to confirm or reject the device addition:
- A link to log in and review devices (using strong authentication)
- An option to report suspicious activity or block the new device
- Use Secure Messaging Standards For push notifications or in-app alerts:
- Use end-to-end encryption where possible
- Authenticate the sender (your bank) to prevent phishing
- Use signed messages to prove alert integrity
- Limit Alert Fatigue
- Only send alerts for first-time or unusual device enrollments
- Avoid repetitive alerts that may desensitize users
5. Tie to Real Identity When Required (eKYC Integration)
Many banking operations require linking authentication to a user’s legal identity (e.g., for onboarding or high-value transfers).
✅ Best Practices
- Use DocAuth during registration to link the passkey to a verified identity
- Optionally, sign identity attributes using the FIDO credential (e.g., name, KYC timestamp)
- Store metadata like device model and verification level with the public key
🔍 This enables identity-bound login, where the person using the device is provably the same person who completed identity verification.
6. Support Multi-Device & Recovery (Securely)
Passkeys allow users to log in from multiple devices, but banks must manage this without weakening security.
✅ Best Practices
- Allow device registration only from a verified, logged-in session
- Send alerts for new device enrollments (see above)
- Validate each new device via device attestation
- Use step-up authentication (e.g., DocAuth or re-auth) for sensitive actions on new devices
- Apply policy enforcement for recovery or re-registration paths
🔍 By performing device attestation for each device, the bank can confirm that it’s a trusted platform (not a rooted phone or emulator) and meets hardware security requirements.
7. Regulatory Compliance & Auditing
✅ How FIDO aligns with key regulations:
| Regulation | FIDO Fit |
|---|---|
| PSD2 (EU) | FIDO satisfies Strong Customer Authentication (2 of 3 factors: possession + biometric) |
| GDPR | Biometric and PIN data never leave the device, respecting privacy |
| FFIEC (US) | Meets requirements for multifactor and device security |
| BaFin (Germany) | FIDO + identity binding supports compliant onboarding |
Auditing Tips:
- Log authenticator type, user verification status, and device attestation result
- Track failed login attempts and suspicious patterns
- Feed logs into your SIEM system for fraud analysis and forensic readiness
Bonus: Transaction Binding with FIDO
For added protection on high-value or sensitive transactions, implement transaction binding.
- The FIDO device signs a challenge that includes transaction details (e.g., amount, account number)
- The user sees and confirms the exact transaction on-screen
- Local biometric verification completes the authorization
🔍 This prevents man-in-the-browser attacks, where malware could secretly alter a transaction after user input.
Summary: What a Secure FIDO Setup Looks Like for Banks
| Element | Recommended Practice |
|---|---|
| Authenticator | Hardware-backed, attested |
| Biometric/PIN | Local verification required |
| Identity | Verified via DocAuth or eKYC |
| Recovery | Secure fallback (DocAuth, step-up) |
| Device Trust | Device attestation + policy enforcement |
| Device Management | User device dashboard, revoke, migration, enrollment recovery |
| Transactions | Use transaction binding |
| Compliance | Align with PSD2, FFIEC, GDPR, BaFin |
Conclusion: FIDO Is Ready for Banking—If Applied Correctly
FIDO provides phishing-proof, user-friendly, and regulation-ready authentication for modern banking.
To use it safely, banks must:
- Rely on hardware-backed devices
- Enforce local verification
- Use identity verification (DocAuth)
- Apply device attestation
- Support secure recovery and device management
- Comply with local financial regulations
Done right, FIDO can cut fraud, reduce support costs, and boost trust—without sacrificing user experience.






