Modern banking apps demand both tight security and a smooth user experience. Whether a user is onboarding instantly or waiting hours for a manual identity check, one challenge remains constant:
How do we securely bind a FIDO2 credential to a specific device without leaving room for impersonation or misuse — even if the identity verification is delayed?
The Challenge – Power a Smooth Transition
During onboarding, users might go through identity checks such as:
- ID scanning
- Face or video verification
- Document upload for manual review
These checks can happen immediately — or be delayed for hours or days.
Without protection, a delay opens the door to threats like:
- Token theft
- Impersonation
- Replay or reuse of FIDO registration links or codes
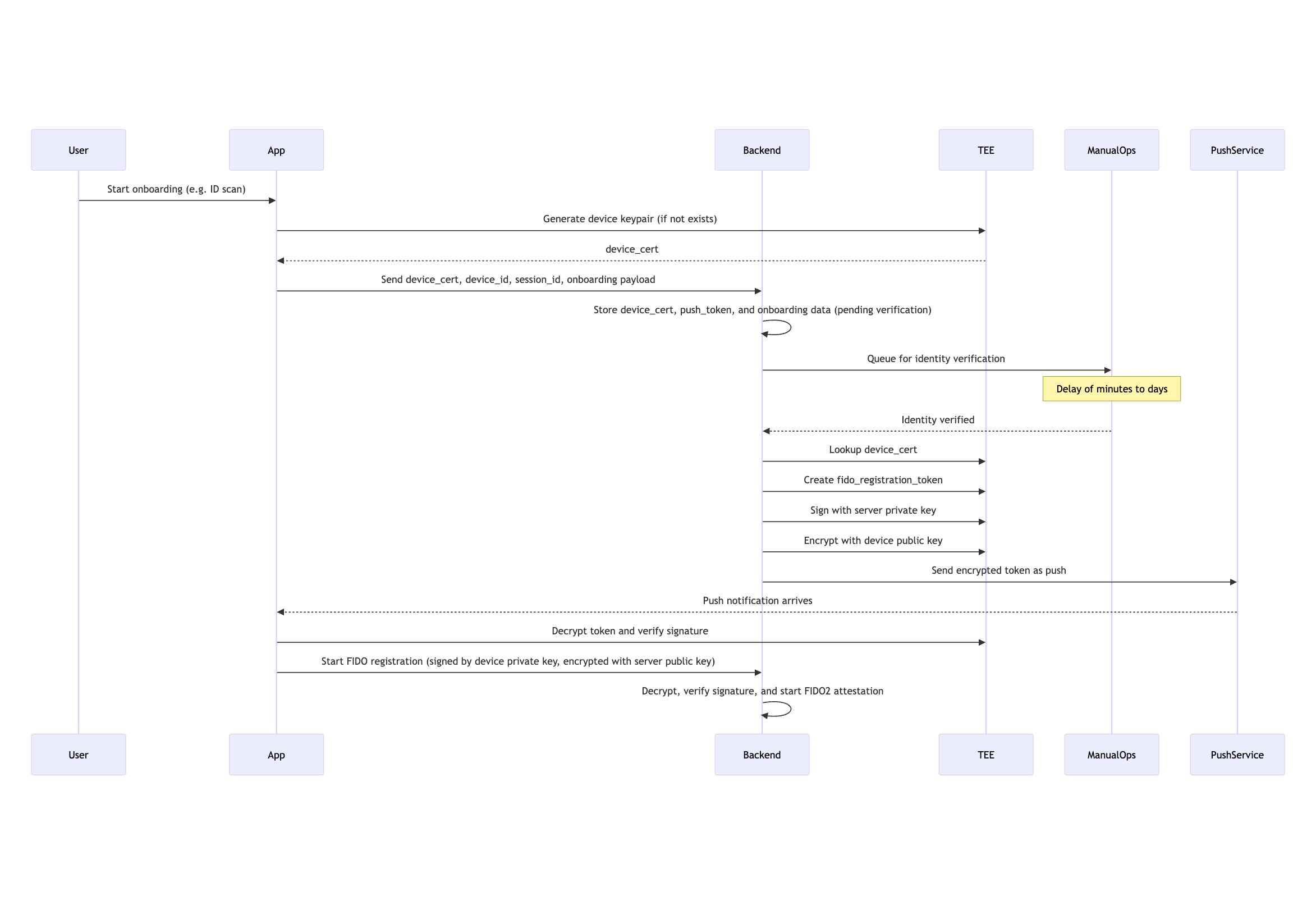
The Solution: Secure Token + Device Binding Flow
The flow we apply works securely with immediate or delayed identity verification by relying on public-key cryptography and secure enclaves (TEE).
1. Initial Onboarding (App → Backend)
- App generates a device keypair in secure hardware (TEE/Secure Enclave)
- Sends the device public key (
device_cert) and metadata to the backend
2. Identity Verification
- The backend queues the onboarding for manual or automatic verification
- Once verified (immediately or later), the backend:
- Generates a short-lived
fido_registration_token - Signs it with the backend private key
- Encrypts it with the device’s public key
- Sends it via push notification to the app
- Generates a short-lived
3. Secure FIDO2 Registration (App → Backend)
- The app decrypts and verifies the token
- Sends a signed and encrypted FIDO2 registration request
- Signed using device private key
- Encrypted using server’s public key
What This Secures
| Risk | Mitigation |
|---|---|
| Token misuse/theft | Token is encrypted for device — only it can decrypt |
| Server spoofing | Signature from server is verified by app |
| Device impersonation | Device proves possession of private key in registration |
| Replay or reuse | Tokens are one-time use and time-limited |
| Delayed identity verification | Token is only issued after verification is complete |
Why It Works So Well
This approach supports both:
- Real-time onboarding (e.g., automated face scan + instant registration)
- Delayed onboarding (e.g., manual ID verification within 24–48h)
And still guarantees:
- FIDO2 is only usable on the correct device
- The device was verified before FIDO2 keys were registered
- No sensitive tokens can be intercepted or misused
Bottom Line
This flow allows banks to combine:
- The zero-trust security of FIDO2
- The flexibility of delayed or immediate identity verification
- The cryptographic assurance of secure device binding
Whether your onboarding process takes seconds or days — this is how to do secure FIDO2 device activation right.
Why FIDO2 is the right choice, please read here






